Checkpoint tags-4 WC blog 243
clothing security tags-3
Clothing security-4
Security tags on clothes-3
Employee Theft Of Clothes Can Be Curtailed With Checkpoint Tags
Apparel store owners and managers, where do you think the majority of your store shrinkage is occurring? Your first reaction may be shoplifters and that would be a good guess. It would also be the wrong guess. According to the 2014-2015 Global Retail Theft Barometer, North American Apparel Specialist Retailers experienced 44% of their losses from dishonest employees (pg. 54). Shoplifting did follow at a close 41% as a cause of shrinkage with vendor/supplier fraud and administrative and non-crime losses accounting for the remaining 16% of losses. Total shortage for Apparel Retailers during this time frame equaled 1.98% so if your store is trending with the national average, how are you addressing the almost 45% of losses in your store taking place due to employee theft? What steps are you taking to address clothing security and protect your bottom line? If you aren’t using Checkpoint tags on apparel you are doing a disservice to your business.
What are Checkpoint tags for clothing? Clothing security tags by Checkpoint are radio frequency sensitive devices that are clipped to garments. When a protected item is carried near a door with a Checkpoint antenna the tag causes the antenna alarm to activate. Lights flash and a loud noise will draw the attention of employees. An employee who responds to an alarm determines the cause of the alarm and can recover merchandise that has not been paid for by the customer/thief. Clothing security tags are a visible deterrent to anyone who may consider trying to steal an item. Most people are familiar with security tags on clothes and will try to find an unprotected item rather than take a chance with setting off the antenna when they are ready to leave. One other advantage of clothing security devices is that they require a special detachment tool to remove them. If someone forcibly removes a tag it damages the garment. If damaged, the merchandise loses its appeal to the thief.
Returning to the point I made at the beginning of the article, can Checkpoint tags prevent that 45% of the losses employee theft may be costing your business? The answer is yes, they can. There are several things to keep in mind to ensure that clothing security is not compromised when it comes to preventing employee theft. One thing I saw during a few of my internal employee investigation cases was that electronic article surveillance antenna alarm activations by an employee were often shrugged off. All alarm activations should be treated with the same response. There is a tendency for co-workers to bond and in doing so there is an inherent trust that forms. Dishonest employees will use this trust to engage in dishonest activity. All employees should understand how to respond to respond to an alarm and how to look for security tags on clothes that may set off that alarm. The same level of response applies to customers and employees with thorough bag checks and receipt inspections.
Clothing security detachment tools must also be properly controlled and accounted for daily. The easiest method is to use the detachment tool that can be secured to the counter and make a check of it part of the daily opening tasks. If you have portable detachers for your employees who stock freight and attach tags to new merchandise, require them to sign their device in and out and a supervisor or manager locks them away. Dishonest employees may try to steal a detachment tool and use it to remove Checkpoint tags and then the clothes they were protecting.
Finally, a daily check of the Checkpoint system should be documented. This inspection does not take long, but it verifies that deactivation units are working, as are the antennas. If an employee knows the antennas are not working the dishonest one will use this knowledge as an opportunity to get merchandise with clothing security tags on them out of the store without creating an alarm.
Security tags on clothes are an effective method of significantly reducing shortage due to employee theft. If you haven’t invested in Checkpoint tags yet, check out what you may be costing yourself.
Clothing Security is important and we can help you with that. Call 1.770.426.0547 and let’s talk.
Apparel store owners and managers, where do you think the majority of your store shrinkage is occurring? Your first reaction may be shoplifters and that would be a good guess. It would also be the wrong guess. According to the 2014-2015 Global Retail Theft Barometer, North American Apparel Specialist Retailers experienced 44% of their losses from dishonest employees (pg. 54). Shoplifting did follow at a close 41% as a cause of shrinkage with vendor/supplier fraud and administrative and non-crime losses accounting for the remaining 16% of losses. Total shortage for Apparel Retailers during this time frame equaled 1.98% so if your store is trending with the national average, how are you addressing the almost 45% of losses in your store taking place due to employee theft? What steps are you taking to address clothing security and protect your bottom line? If you aren’t using Checkpoint tags on apparel you are doing a disservice to your business.
What are Checkpoint tags for clothing? Clothing security tags by Checkpoint are radio frequency sensitive devices that are clipped to garments. When a protected item is carried near a door with a Checkpoint antenna the tag causes the antenna alarm to activate. Lights flash and a loud noise will draw the attention of employees. An employee who responds to an alarm determines the cause of the alarm and can recover merchandise that has not been paid for by the customer/thief. Clothing security tags are a visible deterrent to anyone who may consider trying to steal an item. Most people are familiar with security tags on clothes and will try to find an unprotected item rather than take a chance with setting off the antenna when they are ready to leave. One other advantage of clothing security devices is that they require a special detachment tool to remove them. If someone forcibly removes a tag it damages the garment. If damaged, the merchandise loses its appeal to the thief.
Returning to the point I made at the beginning of the article, can Checkpoint tags prevent that 45% of the losses employee theft may be costing your business? The answer is yes, they can. There are several things to keep in mind to ensure that clothing security is not compromised when it comes to preventing employee theft. One thing I saw during a few of my internal employee investigation cases was that electronic article surveillance antenna alarm activations by an employee were often shrugged off. All alarm activations should be treated with the same response. There is a tendency for co-workers to bond and in doing so there is an inherent trust that forms. Dishonest employees will use this trust to engage in dishonest activity. All employees should understand how to respond to an alarm and how to look for security tags on clothes that may set off that alarm. The same level of response applies to customers and employees with thorough bag checks and receipt inspections.
Clothing security detachment tools must also be properly controlled and accounted for daily. The easiest method is to use the detachment tool that can be secured to the counter and make a check of it part of the daily opening tasks. If you have portable detachers for your employees who stock freight and attach tags to new merchandise, require them to sign their device in and out and a supervisor or manager locks them away. Dishonest employees may try to steal a detachment tool and use it to remove Checkpoint tags and then the clothes they were protecting.
Finally, a daily check of the Checkpoint system should be documented. This inspection does not take long, but it verifies that deactivation units are working, as are the antennas. If an employee knows the antennas are not working the dishonest one will use this knowledge as an opportunity to get merchandise with clothing security tags on them out of the store without creating an alarm.
Security tags on clothes are an effective method of significantly reducing shortage due to employee theft. If you haven’t invested in Checkpoint tags yet, check out what you may be costing yourself.
Clothing Security is important and we can help you with that. Call 1.770.426.0547 and let’s talk.
AA Blog 36
Alpha Thunder tag: 5
Tablet theft: 3
Our Reliance On Technology Has Created A Vulnerability We Cannot Ignore. Let The Alpha Thunder Tag Protect You From An Unauthorized Data Breach
My husband and I are pretty active and in the summer we love to play softball, although we both tend to be very accident prone. This year was no exception, with both of us ending up in the emergency room. I had the misfortune of tripping as I was running to third base, I know graceful right? Unfortunately for me I just happened to fall directly on a rock, which resulted in a quarter-sized hole in my knee cap, which went down to the bone. I did however finish the game before I took myself to the emergency room. I know sounds crazy, but you can’t sew up a hole, which was confirmed by the doctors. Needless to say I still spent some time in the hospital getting the wound cleaned and wrapped. It wasn’t a pleasant experience, but the hospital staff was very kind and friendly during my brief visit. During my appointment I did notice that the nurses and doctors had significantly improved their efficiency, which got me in and out much quicker than I anticipated. It seems like technology has continued to improve efficiency in many areas of our lives. The medical field appears to be no exception to this, as I watched everyone documenting and retrieving medical information from readily accessible tablets and other handheld devices. As they documented my personal information and health history in front of me, I was intrigued by this paperless methodology. I couldn’t help but think about how convenient it must be to be able to alleviate the need for paper documents, and the time it must save maintaining those records electronically. Although convenient, it did make me think about the physical security of the device, and more importantly the information contained on it. The hospital must take some precautions to prevent the theft of these devices to avoid liability and unauthorized access to personal health information. From a loss prevention standpoint my thoughts immediately went to the Alpha Thunder tag, as a possible solution to prevent tablet theft in the medical field.
Unfortunately in this day and age, data breaches are very common, and criminals tend to capitalize on these types of weaknesses and exposures. The Alpha Thunder tag can prevent tablet theft or theft of other electronic devices such as iPads, laptops or other equipment that are designed to store sensitive information. I have used the Alpha Thunder tag in my stores to help protect some of my merchandise, which has been very successful. I think this application could be very effective in protecting electronic devices used in the medical field as well. These devices are simply placed onto the tablet or device with an adhesive, which allows for convenient placement. They are equipped with electronic article surveillance, which alerts staff when a theft or breach has occurred. Hospitals and clinics would simply install antennas at the entry/exit points and equip their devices with the tag. If someone attempts to remove the device or leave with the tablet, it sounds an audible alarm. This would help protect the medical entity from exposing sensitive patient information, which can lead to lawsuits and monetary settlements. The tag is equipped with a switch that activates and deactivates the alarm, so the device could be moved between clinics, divisions or deactivated when needed. These tags are re-useable and provide a cost-efficient means to protect your property from theft.
I would venture to say that there are plenty of businesses, retailers and manufacturers out there that could also benefit from the Alpha Thunder tag. Whether they are trying to protect employee information or simply protecting trade secrets, technology has created a need to protect against tablet theft. The medical field is a great example of this, but I could think of a dozen or more situations in which these tags would be effective. Don’t be vulnerable to data breaches and theft of your electronic devices, protect yourself and reduce your liability.
Alpha Thunder tags are important and we can help you with it. Call 1.770.426.0547 and let’s talk.
My husband and I are pretty active and in the summer we love to play softball, although we both tend to be very accident prone. This year was no exception, with both of us ending up in the emergency room. I had the misfortune of tripping as I was running to third base, I know graceful right? Unfortunately for me I just happened to fall directly on a rock, which resulted in a quarter-sized hole in my knee cap, which went down to the bone. I did however finish the game before I took myself to the emergency room. I know sounds crazy, but you can’t sew up a hole, which was confirmed by the doctors. Needless to say I still spent some time in the hospital getting the wound cleaned and wrapped. It wasn’t a pleasant experience, but the hospital staff was very kind and friendly during my brief visit. During my appointment I did notice that the nurses and doctors had significantly improved their efficiency, which got me in and out much quicker than I anticipated. It seems like technology has continued to improve efficiency in many areas of our lives. The medical field appears to be no exception to this, as I watched everyone documenting and retrieving medical information from readily accessible tablets and other handheld devices. As they documented my personal information and health history in front of me, I was intrigued by this paperless methodology. I couldn’t help but think about how convenient it must be to be able to alleviate the need for paper documents, and the time it must save maintaining those records electronically. Although convenient, it did make me think about the physical security of the device, and more importantly the information contained on it. The hospital must take some precautions to prevent the theft of these devices to avoid liability and unauthorized access to personal health information. From a loss prevention standpoint my thoughts immediately went to the Alpha Thunder tag, as a possible solution to prevent tablet theft in the medical field.
Unfortunately in this day and age, data breaches are very common, and criminals tend to capitalize on these types of weaknesses and exposures. The Alpha Thunder tag can prevent tablet theft or theft of other electronic devices such as iPads, laptops or other equipment that are designed to store sensitive information. I have used the Alpha Thunder tag in my stores to help protect some of my merchandise, which has been very successful. I think this application could be very effective in protecting electronic devices used in the medical field as well. These devices are simply placed onto the tablet or device with an adhesive, which allows for convenient placement. They are equipped with electronic article surveillance, which alerts staff when a theft or breach has occurred. Hospitals and clinics would simply install antennas at the entry/exit points and equip their devices with the tag. If someone attempts to remove the device or leave with the tablet, it sounds an audible alarm. This would help protect the medical entity from exposing sensitive patient information, which can lead to lawsuits and monetary settlements. The tag is equipped with a switch that activates and deactivates the alarm, so the device could be moved between clinics, divisions or deactivated when needed. These tags are re-useable and provide a cost-efficient means to protect your property from theft.
I would venture to say that there are plenty of businesses, retailers and manufacturers out there that could also benefit from the Alpha Thunder tag. Whether they are trying to protect employee information or simply protecting trade secrets, technology has created a need to protect against tablet theft. The medical field is a great example of this, but I could think of a dozen or more situations in which these tags would be effective. Don’t be vulnerable to data breaches and theft of your electronic devices, protect yourself and reduce your liability.
Alpha Thunder tags are important and we can help you with it. Call 1.770.426.0547 and let’s talk.
What are the differences between Checkpoint Systems and Alpha High Theft Solutions 1 alarm, 2 alarm and 3 alarm solutions?
The following is a brief explanation of the Alpha High Theft Solutions 1, 2 and 3 Alarm products functionality.
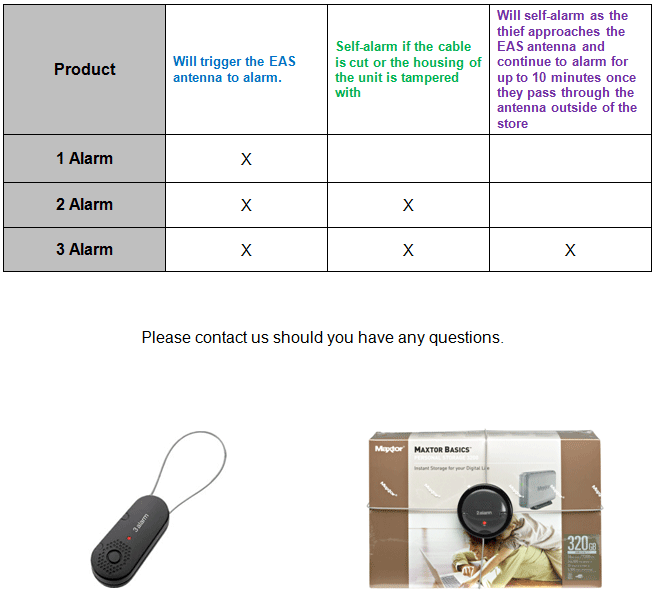
1,2, and 3 alarm solutions encompass individual and combined security solutions for whatever your loss issue is.
The functionality begins with our Alpha 1 Alarm device and it will activate the Checkpoint Systems Electronic Article Surveillance antenna if a breach occurs.
The Alpha 2 Alarm device has added security that in addition to activating upon breach it will activate if the device is cut or even tampered with. The cable is coated and made from aircraft strength cable for extreme durability and reliability. The coating on the cable not only protects the merchandise from theft but protects it from the device.
For our most complete device the Alpha 3 Alarm Includes the same as 1 and 2 alarm actions, activation upon breach and activation upon tampering or cutting, It also will continue alarming with an extended range protection at 95 Decibels for up to 10 minutes after shoplifter has left the premises. The standard decibel is a ratio of how much acoustical energy we hear with and for human conversation is 35 to 45 DCB. This technology provides an extra piece of mind when added to your security solution to stop shoplifting.